Database design
SQL
I design normalized schemas with entity relationship diagrams to eliminate data redundancy, maintain referential integrity, and create efficient database structures. My SQL skills enable effective database management across multiple dimensions. For data retrieval and analysis, I write complex queries utilizing inner and outer joins to combine data from multiple tables, subqueries to filter results based on aggregate conditions, and window functions for advanced analytics. For database administration, I develop stored procedures that improve performance by reducing network traffic and enabling code reuse, implement indexes strategically to accelerate query execution without excessive storage overhead, and configure user permissions and roles to enforce least privilege access. I also perform query optimization by analyzing execution plans, troubleshoot performance bottlenecks, and ensure data integrity through proper use of constraints, foreign keys, and transaction management
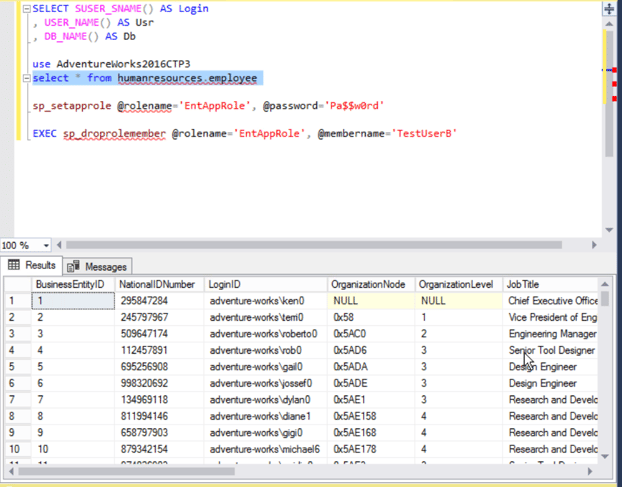
Common Attack Vectors
I address OWASP Top 10 vulnerabilities with emphasis on injection attacks and cross-site scripting. SQL injection remains a critical threat where attackers manipulate database queries, enabling attackers to bypass authentication, extract sensitive data, or execute administrative commands. I've identified SQLi variants including error-based, blind boolean, and time-based attacks during security assessments. Cross-site scripting enables attackers to inject malicious scripts into web pages viewed by other users, resulting in session hijacking, credential theft, or malware distribution. Both vulnerabilities stem from trust boundary violations and insufficient input/output handling, requiring defense-in-depth strategies across application and database layers.
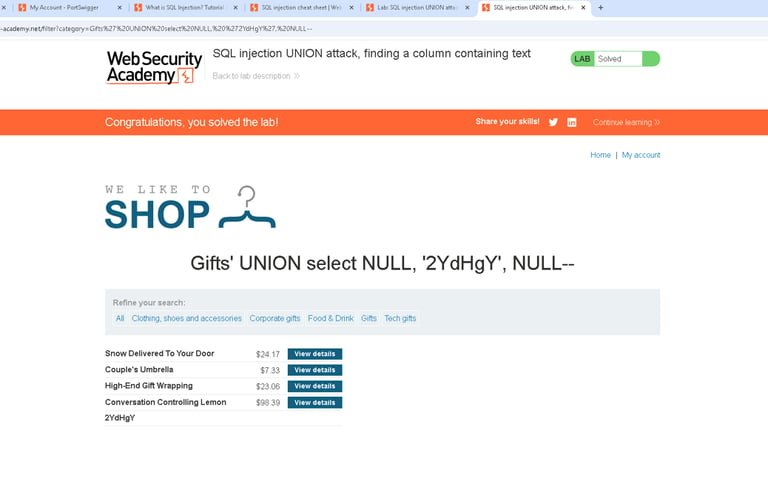
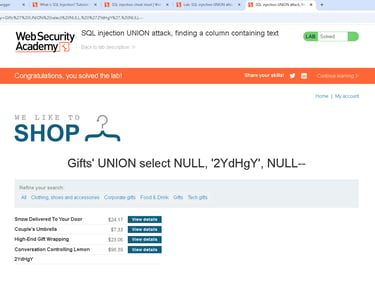
Secure Configuration Management
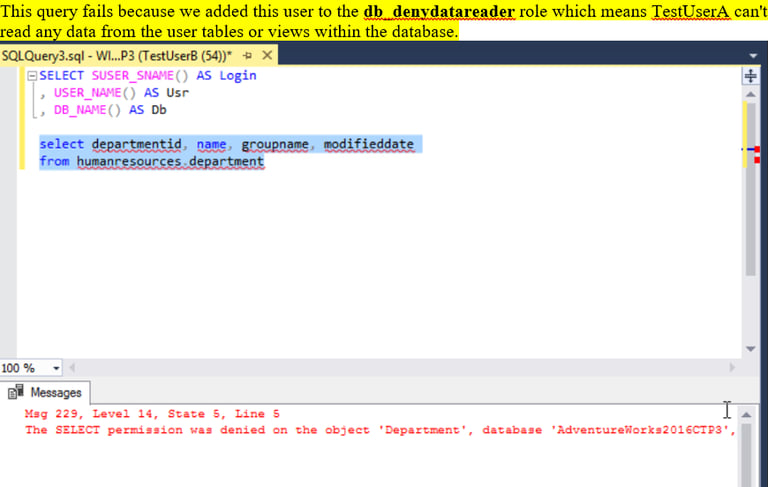
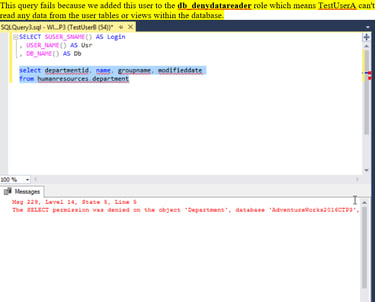
I implement comprehensive database security controls addressing injection attacks, unauthorized access, and data exposure. At the application layer, I enforce parameterized queries and prepared statements that prevent SQL injection by separating query structure from user-supplied data. Database architecture follows least privilege principles—users access data through stored procedures rather than direct table permissions, leveraging ownership chaining to execute privileged operations without granting underlying object access. I restrict access to high-risk features like xp_cmdshell and OPENROWSET, implement row-level security for multi-tenant data isolation, and encrypt sensitive columns using Transparent Data Encryption. My approach includes regular security assessments, automated vulnerability scanning, comprehensive audit logging, and disaster recovery testing to ensure resilience against both external attacks and insider threats
Contact Me
contact@alexanderrodriguez-portfolio.com
© 2025. All rights reserved.