Networking
Network Traffic Analysis
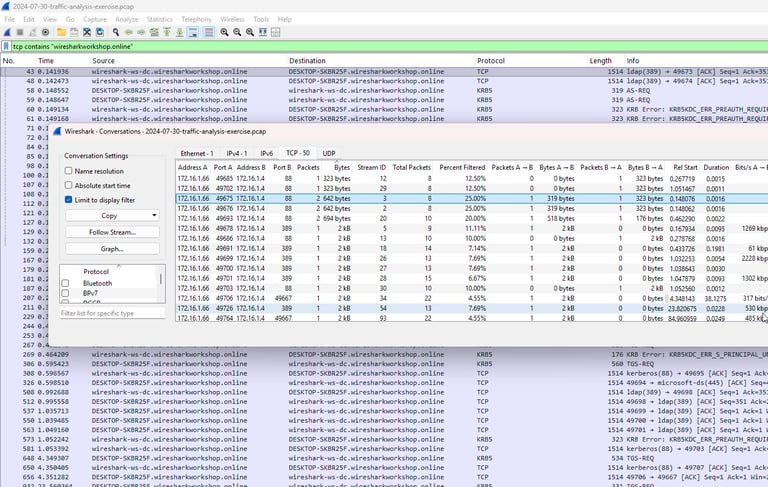
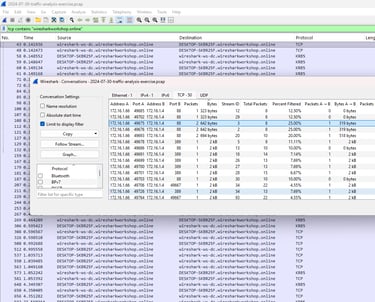
I leverage Wireshark for packet-level analysis during incident response, malware investigations, and network troubleshooting. I apply display filters and conversation tracking to isolate suspicious traffic patterns, reconstruct TCP streams, and identify protocol anomalies that indicate compromise. During malware analysis, I extract indicators of compromise including C2 server IPs, callback URIs, and exfiltrated credentials by examining HTTP POST requests, DNS queries, and SMB traffic. This granular visibility enables me to detect threats that bypass traditional security controls, such as covert channels, beaconing behavior, and lateral movement attempts.
Network Intrusion Detection
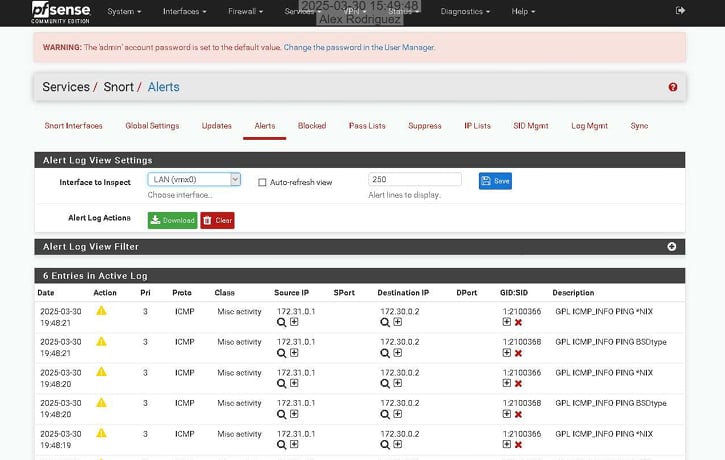
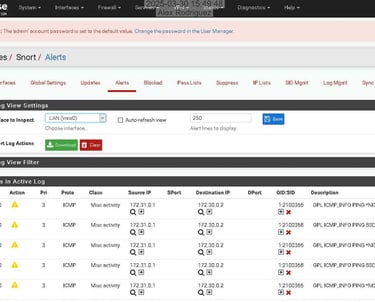
I deploy and manage Snort IDS on pfSense infrastructure to detect network-based threats through signature and anomaly-based analysis. I configure and tune community and custom rulesets to identify exploit attempts, lateral movement traffic, and command-and-control beacons while reducing alert noise through suppression lists and threshold tuning. I forward Snort detections to Splunk via syslog, enabling centralized security monitoring where network alerts are correlated with endpoint, firewall, and authentication events to provide comprehensive attack visibility and streamline incident investigation.
Router and Switch Configuration
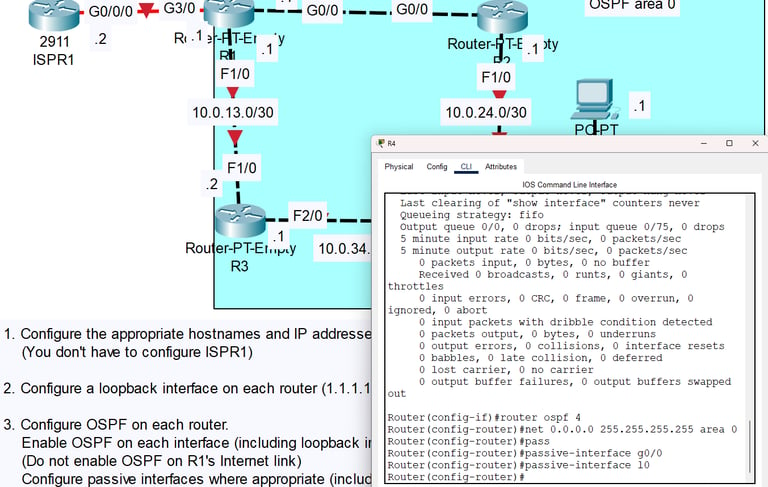
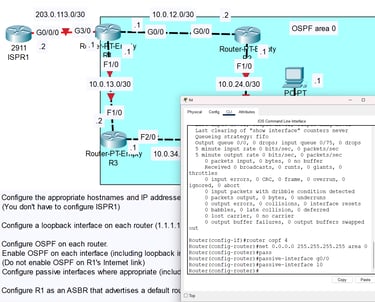
I configure and troubleshoot enterprise network infrastructure with proficiency aligned to Cisco CCNA certification standards. My core competencies include IP addressing and subnetting using VLSM for optimized address allocation, implementing VLANs for logical network segmentation, and configuring inter-VLAN routing to control traffic flows between isolated broadcast domains. I secure network access through port security features like MAC address filtering, dynamic ARP inspection, and DHCP snooping to prevent unauthorized devices and spoofing attacks. My routing expertise spans static routes, default gateways, and dynamic protocols including OSPF for enterprise environments. I configure spanning tree protocol to prevent loops, establish trunk links with 802.1Q tagging, implement wireless controller configurations with WPA3 Enterprise authentication, and leverage network automation through APIs for configuration management and monitoring integration
Contact Me
contact@alexanderrodriguez-portfolio.com
© 2025. All rights reserved.