Security Operations
Security Monitoring
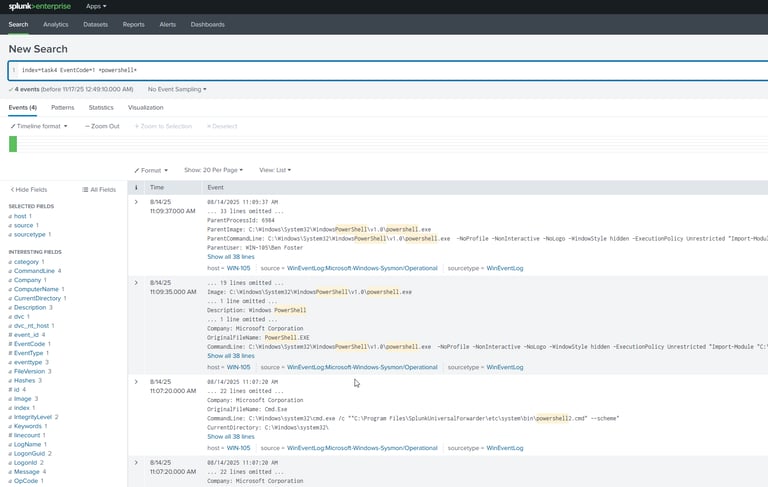
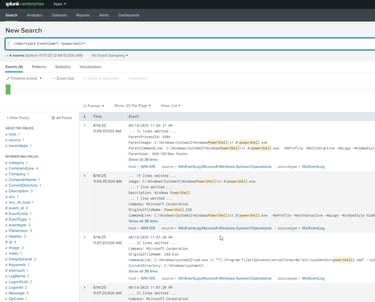
I leverage Splunk for enterprise security monitoring, threat detection, and incident investigation across diverse data sources including endpoint telemetry, network logs, and cloud infrastructure. I develop SPL queries and correlation searches to identify MITRE ATT&CK techniques like lateral movement, privilege escalation, and data exfiltration patterns that indicate compromise. During investigations, I pivot across normalized logs to reconstruct attack timelines, correlate indicators of compromise (IoCs), and identify root cause. I continuously tune detection rules to optimize signal-to-noise ratios, create custom dashboards for SOC visibility, and develop automated alerting workflows that accelerate response times while reducing analyst burnout,
Incident Response
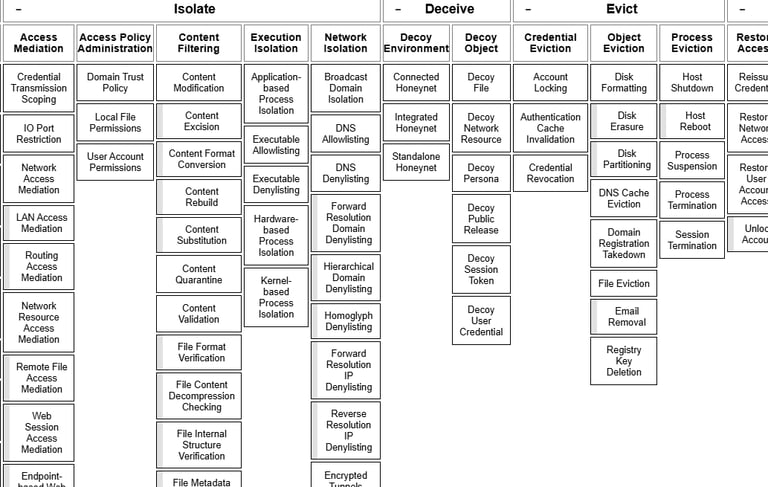
I employ the MITRE D3FEND framework to implement evidence-based defensive countermeasures aligned with specific attack techniques. My incident response approach integrates core D3FEND actions like isolation, eviction, and restoration to minimize threat impact and accelerate recovery. By mapping defensive capabilities to adversary tactics, I develop proactive security postures rather than purely reactive alert-driven responses.
Digital Forensics
I perform digital forensics investigations using both static and live acquisition techniques to preserve critical evidence. Using FTK Imager, I create forensically sound disk images that maintain data integrity and chain of custody. For volatile evidence, I capture system memory with PMem and analyze it using Volatility. This reveals active processes, injected code, and network connections that traditional disk forensics may miss. I utilize Autopsy to efficiently examine artifacts through timeline analysis and file carving, recovering deleted files attackers attempted to conceal and correlating activity across multiple evidence sources.
Contact Me
contact@alexanderrodriguez-portfolio.com
© 2025. All rights reserved.